LinkedIn's SAST: GitHub Actions, CodeQL, & Semgrep
Alps Wang
Feb 7, 2026 · 1 views
Leveling Up: SAST at LinkedIn
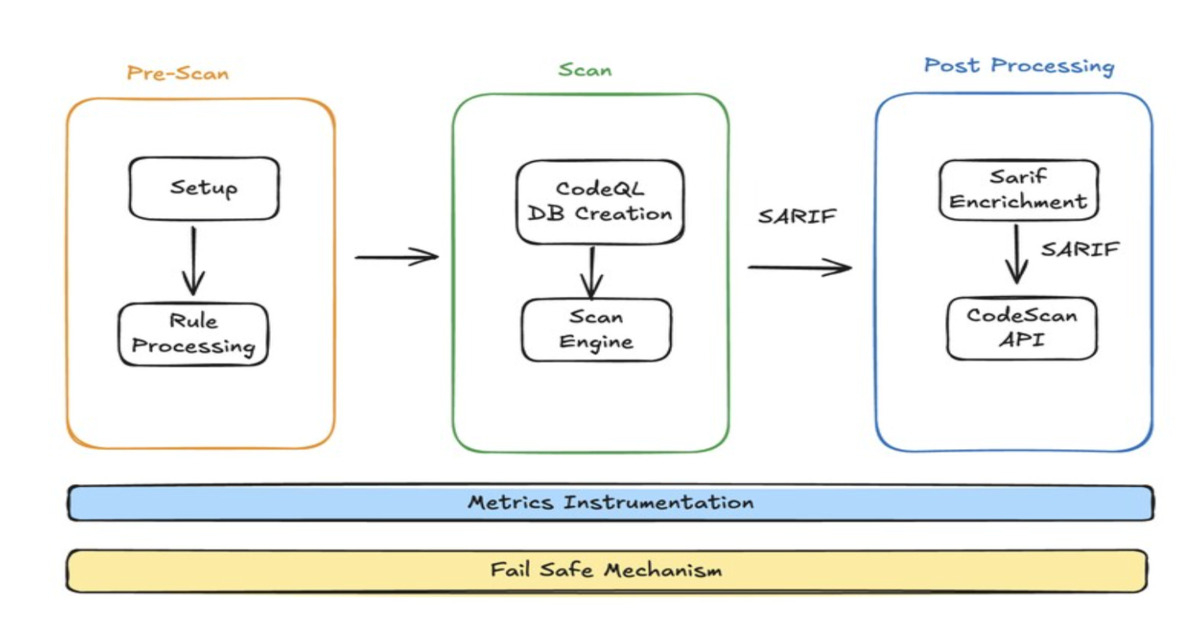
This article highlights LinkedIn's strategic shift towards a more integrated and efficient Static Application Security Testing (SAST) pipeline. The core innovation lies in the adoption of GitHub Actions, CodeQL, and Semgrep to automate and standardize code scanning within a multi-repository environment. This approach allows for consistent enforcement of security policies, faster feedback loops for developers, and improved visibility into the overall security posture. The use of a 'stub workflow' to propagate changes across numerous repositories, coupled with drift management, is a particularly clever solution to the scalability challenges inherent in large-scale deployments. The article also emphasizes the importance of developer-first security, minimizing disruptions, and providing clear remediation guidance. While the article provides a good overview, it could benefit from more detailed technical insights, such as specific performance metrics of the new pipeline compared to the legacy system. Additionally, a deeper dive into the custom workflows implemented by LinkedIn engineers would further enhance the article's value. The focus on the SARIF standard for results normalization is commendable, but the article could explore the challenges and best practices around effectively utilizing SARIF within the context of the chosen tools. Finally, there's a missed opportunity to discuss how this SAST pipeline integrates with other security measures, such as dependency scanning and secret detection, which the article only briefly mentions.
Key Points
- LinkedIn redesigned its SAST pipeline to leverage GitHub Actions, CodeQL, and Semgrep for consistent code scanning across its multi-repository environment.
- The new architecture prioritizes developer-first security, extensibility, resilience, and observability.
- A 'stub workflow' and drift management system solve the challenges of propagating changes across numerous repositories.
- Enforcement is handled through GitHub repository rulesets, blocking pull request merges until scans complete.
- Safety mechanisms, including kill switches and fallback behavior, are implemented to prevent workflow disruptions.
📖 Source: LinkedIn Leverages GitHub Actions, CodeQL, and Semgrep for Code Scanning
Related Articles
Comments (0)
No comments yet. Be the first to comment!
